Forensic Readiness in Critical Infrastructures
5/24/2021
 According to various studies [3] [4] UK companies losses reach up to 37 billion euro per year (27 billion pounds), which is comparative to the European Commission’s budget in Innovation, Research and Development over a three-year period for the entire Horizon 2020 program. Across the European Union, the “average cost of cybercrime in Europe has risen steeply to $57,000 (€50,000) per incident” [5], while recent figures also show that the median cost to companies that suffered cyber incidents and breaches jumped to €50,000 over the past 12 months (2019-2020), representing a near six-fold increase on the previous year’s €9,000.
According to various studies [3] [4] UK companies losses reach up to 37 billion euro per year (27 billion pounds), which is comparative to the European Commission’s budget in Innovation, Research and Development over a three-year period for the entire Horizon 2020 program. Across the European Union, the “average cost of cybercrime in Europe has risen steeply to $57,000 (€50,000) per incident” [5], while recent figures also show that the median cost to companies that suffered cyber incidents and breaches jumped to €50,000 over the past 12 months (2019-2020), representing a near six-fold increase on the previous year’s €9,000.
Currently, the approach of the majority of organisations to cyber-incidents focuses on business continuity and disaster recovery. However, this approach often includes actions that contradicts the principles of forensic investigations. Organizations tend to be reactive to cyber-incidents, meaning that once a security incident or data breach occurs their first course of action is to try to handle it and perform forensic investigations, followed by actual evidence collection.
Evidence
What is evidence? The Compact Oxford English Dictionary defines “evidence” as [22] :
evidence (noun): The available body of facts or information indicating whether a belief or proposition is true or valid
1.1 Law Information drawn from personal testimony, a document, or a material object, used to establish facts in a legal investigation or admissible as testimony in a law court.
1.2 Signs or indications of something.
In this blog we are concerned with both of the above definitions, and we define “evidence” in the broadest sense as any recordable event, or an artefact of an event, that can be used towards understanding the cause and nature of the observed incident/event.
Digital and Network Forensics
According to [10] forensics is: “the application of scientific knowledge to legal problems, especially scientific analysis of physical evidence, as from a crime scene”. The forensics process is dominated by ruling out potential explanations for the security events under investigation. Adopting E. F. Schumacher, great truths of philosophical map making, as described in his book “A Guide for the Perplexed”, we can reason that forensics is a convergent problem where cybersecurity is a divergent one. Simply putting it attempted solutions gradually converge on one answer.
Multiple definitions exist regarding Digital Forensics. According to [7] Digital Forensics can be defined as “the use of computer and information systems (IS) knowledge, coupled with legal knowledge, to analyze in a legally acceptable manner digital evidence acquired, processed and stored in a way that is legally acceptable”. According to [9] Digital Forensics science corresponds to the “application of computer science and investigate procedures for a legal purpose involving the analysis of digital evidence after proper search authority, chain of custody, validation with mathematics, use of validated tools, repeatability, reporting, and possible expert presentation.”
According to [8] Network Forensics can be defined as "The use of scientifically proved techniques to collect, fuse, identify, examine, correlate, analyse, and document digital evidence from multiple, actively processing and transmitting digital sources for the purpose of uncovering facts related to the planned intent, or measured success of unauthorized activities meant to disrupt, corrupt, and or compromise system components as well as providing information to assist in response to or recovery from these activities."
Network forensics is a sub-branch of digital forensics, relating to the monitoring and analysis of network traffic for the purposes of gathering information, including legal evidence. Network forensics is the art of capturing, storing and analysis of host and network-based evidence, aiming to identify the source of a network attack. Any forensic process aims to identify profound information in and about the network and the infrastructure not previously known.
Digital and network forensics are mainly used for investigations that aim to address legal issues and are likely to end up in court; hence, the emphasis on legal value of collected evidence. They are complex processes in which methodologies, tools and human intelligence combine for the purpose of investigation.
Chain of custody
When an incident occurs, evidence should be collected and stored securely, while at the same time, it should be protected against degradation, considering that evidence is extremely volatile and can be easily lost or distorted. When handling evidence, careful registration is very important, as it ensures the integrity and traceability of the evidence from origin to the courtroom. Breaches of this integrity affect the legal value of the evidence. Lack of strict control over the personnel responsible for the evidence, at any given point of time, may result in its degradation or compromise.
Furthermore, to preserve evidence integrity, we should document, preserve and make available for review all activities relating to the seizure, examination, storage, or transfer of digital evidence. Any breach to this integrity will directly affect the legal value of the proof.
Any organization can carry out digital investigations for own purposes, without the need to handle evidence in a legally acceptable manner. However, in case something is uncovered that requires legal action (e.g., espionage, fraud), it necessitates that all evidence presented in a court must be collected and documented in a legally acceptable manner for admissibility.
These issues are addressed by the Chain of Custody process that validates the collection, storage, movement and protection of evidence. It provides the forensic link, an audit trail of ‘who did what’ and ‘when it happened’ to a particular piece of evidence. A good monitoring chain can help prove that the evidence in the chain was never left without supervision. Moreover, lack of strict control over who is responsible for the evidence, at any given point of time, may result in its degradation or compromise. An example of a CoC form can be downloaded from the National Institute of Standards and Technology (NIST) website.
Forensic Readiness
Having a Forensic Readiness Plan ensures that forensic investigations and any evidence discovered can be handled and presented so that the organization does not lose a case.
Multiple definitions exist regarding Forensic Readiness. According to [1] Forensic readiness is defined as “…the ability of an organisation to maximise its potential to use digital evidence whilst minimising the costs of an investigation”. According to [19], Forensic Readiness is “having an appropriate level of capability in order to be able to preserve, collect, protect and analyze digital evidence so that this evidence can be used effectively: in any legal matters; in security investigations; in disciplinary proceeding; in an employment tribunal; or in a court of law.”
As literature review reveals, forensic readiness is a broad subject and includes a number of elements. Forensic readiness is also not well understood since the term is often used interchangeably with the term “information security”. [20]
In some cases, gaining this capability can seem expensive as it involves a number of processes, that require new hardware and software as well as people with specialised skill sets in order to implement any Forensic Readiness Plan. Various studies ([8], [14], [15], [16], [17], [18]) suggest that for a successful network investigation, the network itself must be equipped with the infrastructure to fully support this investigation.
Organisations, in the course of their operation, generate a lot of digital data, that can become central pieces of evidence during a security event investigation. However, not all digital evidence is collected, due to the difference usages of it, including internal purposes, regulatory or legal requirements, or other external reasons. It is thus not easy to forecast when and what digital evidence is necessary. To this extend forensic readiness aims to assist organizations in laying the groundwork for incident readiness, so that retrieval of digital evidence is structured and documented, resulting in digital evidence being appropriately collected and stored even “before an incident occurs”, without services interruption.
As already mentioned, digital evidence is extremely volatile and thus, we should safeguard its integrity, authenticity and traceability from origin to a courtroom. A forensic readiness plan ensures that when digital evidence is required, it will be made available in a legally accepted form. This requires proper processes and policies to be in place, as well as careful planning.
Forensic readiness planning is part of a quality information risk management approach. Risk areas have to be identified and assessed and measures must be taken to avoid and minimize the impact of such risk. Organizations with a good risk assessment and information security framework would find it easier to adopt a forensic readiness plan. [12]
According to [1] a forensic readiness plan should have the following goals:
- To gather admissible evidence legally without interfering with business processes
- To gather evidence targeting potential crimes and disputes that could have adverse impact on an organization
- To allow investigations to proceed at costs proportional to the incident
- To minimize interruption of operations by investigations
- To ensure that evidence impacts positively on the outcome of any legal action
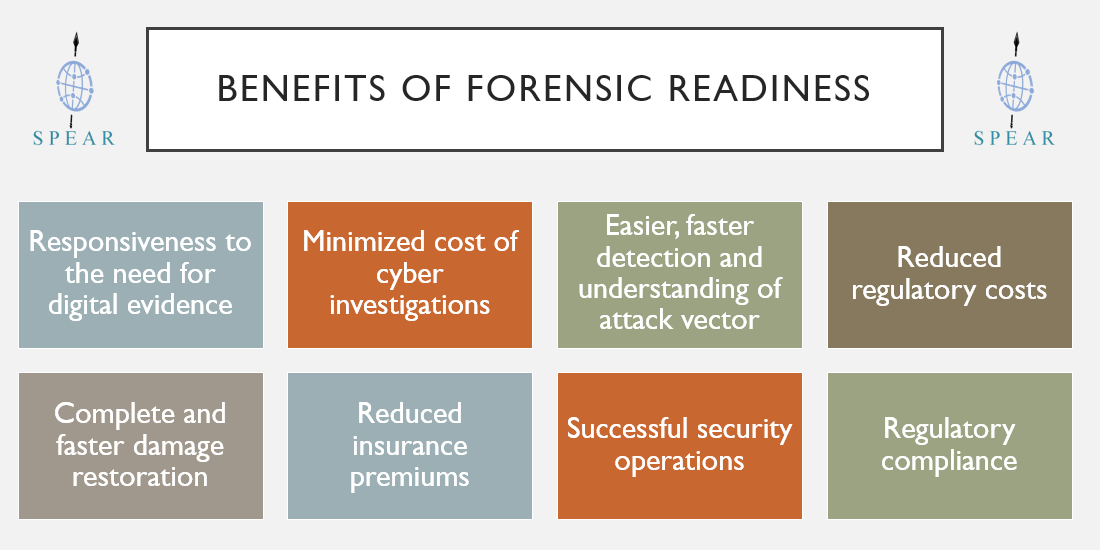
Benefits
The benefits of being forensically ready include: [13], [1]
- Being ready to respond to the potential need for digital evidence. In case an organization has to bring matters to a trial, where digital evidence is required, there will be a need for digital forensics. This in turns requires electronic evidence to be provided quickly and in a forensically sound manner when requested. According to the OSCAR network forensics methodology (presented in [2]) during the collection phase, all data related to a specific event should be collected and stored in an appropriate manner, while ensuring that its integrity is preserved, so that it is readily available when requested. In this phase, the Chain of Custody process is initiated.
- Minimized cost of cyber investigations, since the evidence is gathered and acquired in anticipation of an incident. Costs, time to respond as well as the disruption of operations are reduced and investigations are efficient and rapidly completed.
- Easier and faster detection and understanding of attack vector.
- Reduced costs of regulatory or legal requirements for data disclosure, since the evidence is collected and stored in a proper manner. Regulatory requirements in many EU countries require security and assurance strategies and policies, such data retention, disaster recovery and business continuity, to be in place, and lack of compliance can result in financial penalties. Moreover, failure to provide stored evidence, when requested by regulatory authorities or law enforcement agencies, in an appropriate and timely manner also results in serious adverse costs, to the organization.
- Complete and faster damage restoration and eradication, since post-incident activities could be much optimized with Forensic Readiness, regarding cost, time and effort.
- Reduced insurance premiums, since organisations can prove that are ready to respond to cyber incidents
- Successful security operations program, since potential incidents can be uncovered before they become security incidents or detected early enough before they escalate, while greater cyber-threats can be uncovered, traced and prevented.
- Demonstrates due diligence and good corporate governance of the company's information assets as well as regulatory compliance.
Implementing
An organized approach is key to a successful investigation. As reflected on the results of the “SPEAR Smart-Network Forensics Specification”, organisations should seek for advice/help from a forensic investigator, that can assist them:
- Review and analyse security posture including relevant controls, policies, procedures and skill sets, in order to improve upon what is in place and ensure a good forensic readiness plan.
- Identify security goals, objectives and risk appetite, in order to determine what would be considered significant or relevant risk, what type of incidents should be expected, and how to respond to them.
- Define the scenarios that require digital evidence.
- Identify potential event sources, where they are stored, how they can be accessed, who should be contacted to get permission to access and collect them and how forensically sound they are.
- Identify the resources available for event log collection, aggregation and analysis including evidence storage space, available time, tools, systems, and staff for collection and analysis.
- Identify how the sources of evidence and the network itself will be impacted by evidence collection, network or equipment slowness or outages might be experienced. This helps determine whether devices can be removed from the network, if they can be powered off, if they can be accessed remotely and as a last resort if they can be accessed at specific times or schedule a downtime, to minimise the impact.
- Prioritize sources of evidence, by reviewing the list of possible sources of evidence and identify those that are likely to be of the highest value to the investigation, while also considering the effort needed to obtain them.
- Plan evidence acquisition by discussing and determining which organisation personnel (system and/or network administrators) can provide access to the evidence and what kind of access will be given (physical or remote).
- Enable collection and storage of evidence in a secure and forensically sound manner. Tips for evidence collection include fast and lawful acquisition, creation of cryptographically verifiable copies, analysis only on the copies, usage of reputable and reliable tools and finally documentation of everything we do.
- Establish and maintain a chain of custody policy including appropriate awareness on the importance of maintaining the chain of custody among people handling evidence.
- Select the appropriate methodologies and tools for recovering evidence material from the forensic working image.
- Document evidence-based cases, in a way that they are understandable by non-technical persons like managers, judges, etc. Forensics Technical Report must be factual and defensible in detail. Consequently, all claims must be supported by evidence.
Closing Remarks
Forensic investigations pose a myriad of challenges. To meet these challenges, investigators must carefully assess each investigation and develop a realistic strategy that takes into account both the investigative goals and the available resources. [2]
As Sun Tsu wrote 2,500 years ago: “A victorious army first wins and then seeks battle; a defeated army first battles and then seeks victory.” Strategize first; then collect your evidence and conduct your analysis. By considering the challenges unique to your investigation up front, you will meet your investigative goals most efficiently and effectively. [2]
While organizations are currently aware of the importance and need for business continuity and disaster recovery plans, they fail to recognize the importance of a forensic readiness plan. Organizations, including operators of critical infrastructures, fail to develop a forensic capability, due to culture and budget considerations, and instead they tend to implement a reactive rather than proactive response to security breaches. As a result, evidence is acquired, processed and stored in a way that it is not legally acceptable.
Forensic readiness greatly minimizes these problems, since evidence is collected in anticipation of an incident in a legally acceptable manner and before investigations begin. As a result, time and money are saved. An outdated forensic readiness plan is of little use, so ownership is essential to ensure it is kept up-to-date. To paraphrase Computer Security expert Bruce Schneier, ‘Forensic readiness is a process, not a product’.[21]
References
- Robert Rowlingson,” A Ten Step Process for Forensic Readiness,” International Journal of Digital Evidence, vol. 2, issue. 3, Winter 2004.
- Sherri Davidoff and Jonathan Ham, “Network Forensics, Tracking Hackers through Cyberspace”, 2012, ISBN-13: 978-0-13-256471-7
- The cost of incidents affecting CIIs, Systematic review of studies concerning the economic impact of cyber-security incidents on critical information infrastructures (CII) AUGUST 2016, ENISA
- Cyber-Attacks: Effects on UK companies, Oxford Economics, 2014
- Cost of cybercrime per incident jumps six-fold to €50,000, June 2020, consultancy.eu
- NICS, Forensics Readiness Guidelines, 2011
- Sule, Dauda; “Digital Forensics 101: Case Study Using FTK Imager,” eForensics Magazine, February 2013, https://eforensicsmag.com/download/a-practical-approach-to-malware-memory-forensics-with-eforensics-open-2/
- G. Palmer, “A road map for digital forensic research,” in Digital Forensic Research Workshop, Utica, New York, 2001
- Zatyko, K. (2007). Defining Digital Forensics, Forensic Magazine.
- Dictionary by Merriam-Webster: forensic, https://www.merriam-webster.com/dictionary/forensic
- Sommer, Peter; Digital Evidence, Digital Investigations and E-dislosure: A Guide to Forensic Readiness for Organizations, Security Advisers and Lawyers, 3rd Edition, Information Assurance Advisory Council, March 2013
- Rebecca Wynn, Digital Forensic Readiness Planning and Readiness Checklist in Order to Reduce Business Risk
- Ziela Shidi, BENEFITS OF DIGITAL FORENSIC READINESS, March 2017
- Electronic Crime Scene Investigation: A Guide for First Responders, U.S. Department of Justice: National Institute of Justice, July 2001
- N. Beebe and J. G. Clark, “A hierarchical, objectives-based framework for the digital investigations process.” Digital Investigation, vol. 2, no. 2, pp. 147–167, 2005
- V. Baryamureeba and F. Tushabe, “The enhanced digital investigation process model,” in Digital Forensic Research Workshop, Utica, New York, 2004.
- B. Carrier and E. H. Spafford, “Getting physical with the digital investigation process, “International Journal of Digital Evidence, vol. 2, no. 2, 2003.
- A. Almulhem and I. Traore, “Experience with engineering a network forensics system,” Lecture Notes in Computer Science, vol. 3391, pp. 62–71, Jan. 2005.
- The National Archives; Digital Continuity to Support Forensic Readiness, 2011
- Collie, Jan, “A Strategic Model for Forensic Readiness”, 2018, Athens Journal of Sciences, 5(2) pp. 167–182.
- Karen Green, “Forensic Readiness Plans”, Deloitte Issue 18, 2014
- Oxford Dictionaries Online – English Dictionary,” Oxford Dictionaries, https://en.oxforddictionaries.com/definition/evidence